Setup
The following network setup was used for this exploration:
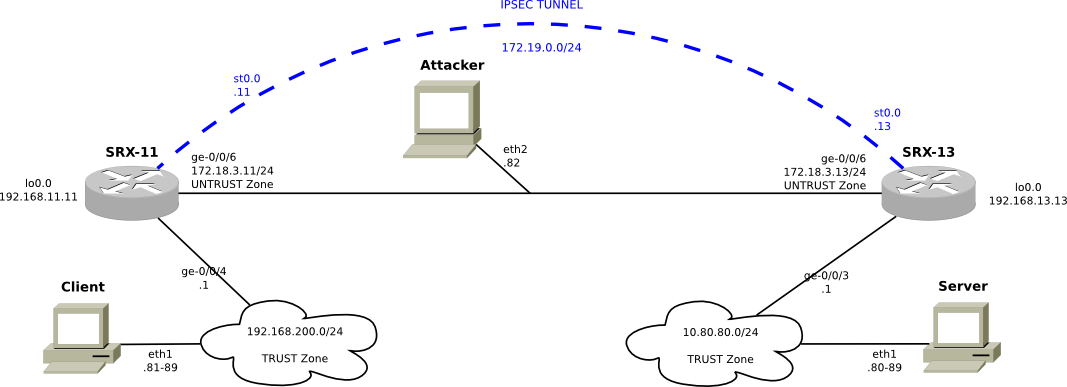
SRX-11 and SRX-13 are Juniper SRX flow mode router/firewalls. They have an IPSEC tunnel between them that we will be playing with to bring it up (and down) using the various flavors and versions of IKE. We have a client and a server that can communicate over each other using the IPSEC tunnel, and we'll just be using them to start up our security associations. On the wire between SRX-11 and SRX-13, we have an attacker that has inserted himself in the path. The attacker will be able to sniff all of the traffic, noteably the IKE exchanges, between the two IPSEC peers. It will also be able to inject traffic.
Although the IPSEC peers here are Juniper SRXes, there isn't anything really specific about what we'll see during the IKE exchanges that is bound to the choice of boxes here. We will be using the trace features on the SRXes to see how they are processing IKE which provides a lot of insight onto how the protocols is working (or not).
SRX-11 has the following configuration on it, complete with an IKEv1 main mode tunnel to SRX-13:
SRX-11 configuration.
interfaces {
ge-0/0/4 {
description "Connection to Client";
unit 0 {
family inet {
address 192.168.200.1/24;
}
}
}
ge-0/0/6 {
description "Connection to SRX-13";
unit 0 {
family inet {
address 172.18.3.11/24;
}
family iso;
}
}
lo0 {
unit 0 {
family inet {
address 192.168.11.11/32;
}
family iso {
address 49.0000.0000.0000.0011.00;
}
}
}
st0 {
unit 0 {
family inet {
address 172.19.0.11/24;
}
}
}
}
routing-options {
static {
route 10.80.80.0/24 next-hop 172.19.0.13;
}
}
protocols {
isis {
level 2 disable;
interface ge-0/0/4.0 {
passive;
}
interface ge-0/0/6.0;
interface lo0.0 {
passive;
}
}
}
security {
ike {
traceoptions {
file ike.log size 10m;
flag ike;
}
proposal IKE-PROPOSAL {
authentication-method pre-shared-keys;
dh-group group1;
authentication-algorithm md5;
encryption-algorithm 3des-cbc;
lifetime-seconds 86400;
}
policy IKE-POLICY {
mode main;
proposals IKE-PROPOSAL;
pre-shared-key ascii-text "$9$iqPQ/CuEclFnclKMN-HqmfFn9ApBRh"; ## SECRET-DATA
}
gateway SRX-13 {
ike-policy IKE-POLICY;
address 192.168.13.13;
external-interface lo0.0;
version v1-only;
}
}
ipsec {
proposal IPSEC-PROPOSAL {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm aes-128-cbc;
lifetime-seconds 1200;
}
policy IPSEC-POLICY {
proposals IPSEC-PROPOSAL;
}
vpn SRX-13 {
bind-interface st0.0;
ike {
gateway SRX-13;
ipsec-policy IPSEC-POLICY;
}
establish-tunnels on-traffic;
}
}
forwarding-options {
family {
iso {
mode packet-based;
}
}
}
policies {
default-policy {
permit-all;
}
}
zones {
security-zone UNTRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
ike;
}
}
interfaces {
lo0.0;
ge-0/0/6.0;
}
}
security-zone TRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
protocols {
ospf;
bfd;
}
}
interfaces {
ge-0/0/4.0;
st0.0;
}
}
}
}
SRX-13 has the following configuration on it, complete with an IKEv1 main mode tunnel to back to SRX-11:
SRX-13 configuration.
interfaces {
ge-0/0/3 {
description "Connection to Server";
unit 0 {
family inet {
address 10.80.80.13/24;
}
}
}
ge-0/0/6 {
description "Connection to SRX-11";
unit 0 {
family inet {
address 172.18.3.13/24;
}
family iso;
}
}
lo0 {
unit 0 {
family inet {
address 192.168.13.13/32;
}
family iso {
address 49.0000.0000.0000.0013.00;
}
}
}
st0 {
unit 0 {
family inet {
address 172.19.0.13/24;
}
}
}
}
routing-options {
static {
route 192.168.200.0/24 next-hop 172.19.0.11;
}
}
protocols {
isis {
level 2 disable;
interface ge-0/0/3.0 {
passive;
}
interface ge-0/0/6.0;
interface lo0.0 {
passive;
}
}
}
security {
ike {
traceoptions {
file ike.log size 10m;
flag ike;
}
proposal IKE-PROPOSAL {
authentication-method pre-shared-keys;
dh-group group1;
authentication-algorithm md5;
encryption-algorithm 3des-cbc;
lifetime-seconds 86400;
}
policy IKE-POLICY {
mode main;
proposals IKE-PROPOSAL;
pre-shared-key ascii-text "$9$cberK8-VYZUHX7UHqmF3SrevX7dbs4JG"; ## SECRET-DATA
}
gateway SRX-11 {
ike-policy IKE-POLICY;
address 192.168.11.11;
external-interface lo0.0;
version v1-only;
}
}
ipsec {
proposal IPSEC-PROPOSAL {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm aes-128-cbc;
lifetime-seconds 1200;
}
policy IPSEC-POLICY {
proposals IPSEC-PROPOSAL;
}
vpn SRX-11 {
bind-interface st0.0;
ike {
gateway SRX-11;
ipsec-policy IPSEC-POLICY;
}
establish-tunnels on-traffic;
}
}
forwarding-options {
family {
iso {
mode packet-based;
}
}
}
policies {
default-policy {
permit-all;
}
}
zones {
security-zone TRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
}
interfaces {
ge-0/0/3.0;
st0.0;
}
}
security-zone UNTRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
ike;
}
}
interfaces {
lo0.0;
ge-0/0/6.0;
}
}
}
}
The SRXes have the ability to capture quite a bit of information about the IKE process by using traceoptions and some IKE debugging commands. Under each SRXes IKE section, we are logging IKE events to a file called ike.log and limiting the size of the file to 10 Megabytes. We have a flag set which will normally just log IKE related events. This takes a commit to start the debug information flowing into the file.
Junos seems to be undergoing a lot of development work in the IKE realm, and the debugging methods for IKE are no exception. As of Junos 11.4R3,
a new method to troubleshoot IKE has appeared in the form of a operational mode request command:
request security ike debug-enable local <ip-address> remote <ip-address> level <level>. During this test, I used Junos 12.1X46-D10.2
and the level portion was hidden. So far this command doesn't seem to be very well documented, but playing with it for a while I learned the
following tidbits of information:
- The level ranges from 1 to 15, with 15 being the most verbose. The default level is 7.
- The default logging location is the kmd file found in the /var/log directory.
- If a file is defined under
security ike traceoptionsthis command will log all information into the file defined there. - If there are flags configured under
security ike traceoptions, these will serve as the defaults for theike debug-enablecommand. - A
commitwith IKE flags under IKE traceoptions will set the debugging level back to the conditions defined by the flags: level, etc.
One other extremely nice thing about this request command, is that it limits the debugging information just to the IKE session defined by the endpoints. Normally if you are using a tracefile, all of the IKE related events are logged here for every session.
All of the logging information captured here is performed with the following commands:
SRX-11 debug commands
request security ike debug-enable local 192.168.11.11 remote 192.168.13.13 level 15
SRX-13 debug commands
request security ike debug-enable local 192.168.13.13 remote 192.168.11.11 level 15
Status of IKE debugging can be checked with the operational mode command show security ike debug-status
Debug status on SRX-11
juniper@SRX-11> show security ike debug-status Enabled flag: all level: 15 Local IP: 192.168.11.11, Remote IP: 192.168.13.13 juniper@SRX-11>
Debug status on SRX-13
juniper@SRX-13> show security ike debug-status Enabled flag: all level: 15 Local IP: 192.168.13.13, Remote IP: 192.168.11.11 juniper@SRX-13>
Debugging can be disabled, or set back to what is defined in the traceoptions for IKE, with the operational mode command request security ike debug-disable.
NOTE: This can be A LOT of debugging information, especially at level 15.Prepare your box with file size limits, archiveing limits, and don't leave these debug commands running when they're not needed!
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Version 0 | C | Plenty |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Router ID - www.blackhole-networks.com |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Area ID - IKE Modes |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| Checksum OK | Construction |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+
| |
+- -+
| PAGE STILL |
+- UNDER -+
| CONSTRUCTION |
+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+