IPSEC with NAT Setup
To explore the effects of NAT on IPSEC, we need a different setup. We still have our client and our host, but we've inserted two more SRX's inbetween them as seen below.
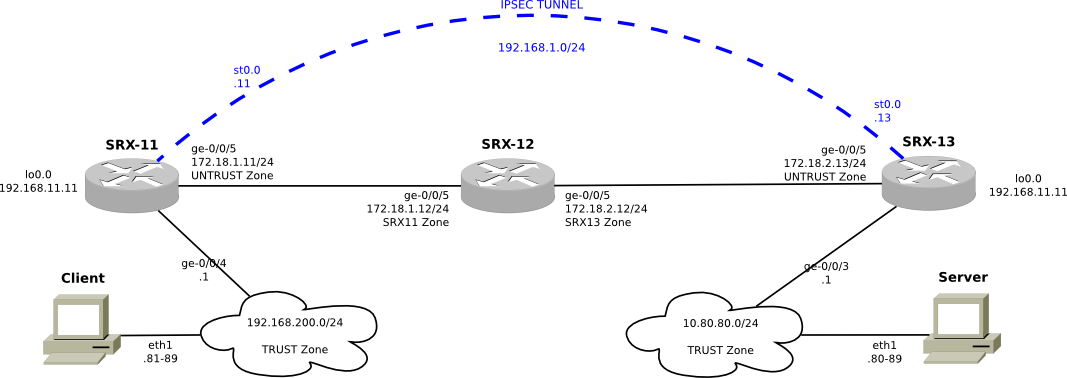
The client is now connected to SRX-11, using the 192.168.200.0/24 subnet for it's LAN which is in SRX-11's TRUST security zone. Likewise, the server is using the 10.80.80.0/24 subnet, which is connected as well to SRX-13's interface which is it's TRUST zone. SRX-11 and SRX-13 are each connected to SRX-12 through their UNTRUST zones. SRX-12 is acting as a firewall, with two separate security zones SRX11 and SRX13 which connect towards their respective SRX neighbors. SRX-12 is acting as a firewall, and has security policies which only allow for some breif diagnostic traffic (in the form of pings), IKE and ESP traffic all flowing from SRX-11 to SRX-13.
Both the client and server retain their multiple IP addresses that they had previously.
SRX-11 and SRX-13 have an IPSEC tunnel between them using secure tunnel interfaces. The IPSEC tunnel travels beteen their two loopback interfaces using 192.168.11.11 and 192.168.13.13 respectively. The IPSEC secure tunnel interfaces belong to the TRUST zones. The IPSEC VPN uses IKE for key exchange. All of the timers have been set to be quite aggressive and time out rather quickly -- so we can see some action!
SRX-11, SRX-12 and SRX-13 trade routing information using IS-IS. SRX-11 and SRX-13 each have static routes pointing to each others LAN subnets over the IPSEC tunnel.
The configurations for the SRXes are listed below.
SRX-11 configuration with IPSEC
interfaces {
ge-0/0/4 {
description "Connection to Client";
unit 0 {
family inet {
address 192.168.200.1/24;
}
}
}
ge-0/0/5 {
description "Connection to SRX-12";
unit 0 {
family inet {
address 172.18.1.11/24;
}
family iso;
}
}
lo0 {
unit 0 {
family inet {
address 192.168.11.11/32;
}
family iso {
address 49.0000.0000.0000.0011.00;
}
}
}
st0 {
unit 0 {
family inet {
address 192.168.1.11/24;
}
}
}
}
routing-options {
static {
route 10.80.80.0/24 next-hop 192.168.1.13;
}
}
protocols {
isis {
level 2 disable;
interface ge-0/0/4.0 {
passive;
}
interface ge-0/0/5.0 {
point-to-point;
}
interface lo0.0 {
passive;
}
}
}
security {
ike {
proposal REKEY-ALOT {
authentication-method pre-shared-keys;
dh-group group1;
encryption-algorithm aes-128-cbc;
lifetime-seconds 180;
}
policy IKE-POL {
proposals REKEY-ALOT;
pre-shared-key ascii-text "$9$byY4ZHqfn/tUj/tuOcSwYgoUjk.PQ36"; ## SECRET-DATA
}
gateway SRX-13 {
ike-policy IKE-POL;
address 192.168.13.13;
external-interface lo0.0;
}
}
ipsec {
proposal SHORT_SA {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm aes-128-cbc;
lifetime-seconds 200;
}
policy IPSEC-POL {
proposals SHORT_SA;
}
vpn SRX-13 {
bind-interface st0.0;
ike {
gateway SRX-13;
ipsec-policy IPSEC-POL;
}
establish-tunnels on-traffic;
}
}
forwarding-options {
family {
iso {
mode packet-based;
}
}
}
policies {
from-zone TRUST to-zone TRUST {
policy ACCEPT-TRUST {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone UNTRUST to-zone UNTRUST {
policy ACCEPT-UNTRUST {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone UNTRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
ike;
}
}
interfaces {
ge-0/0/5.0;
lo0.0;
}
}
security-zone TRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
}
interfaces {
ge-0/0/4.0;
st0.0;
}
}
}
}
SRX-12 configuration
interfaces {
ge-0/0/4 {
unit 0 {
family inet {
address 172.18.1.12/24;
}
family iso;
}
}
ge-0/0/5 {
unit 0 {
family inet {
address 172.18.2.12/24;
}
family iso;
}
}
lo0 {
unit 0 {
family iso {
address 49.0000.0000.0000.0012.00;
}
}
}
}
protocols {
isis {
level 2 disable;
interface ge-0/0/4.0 {
point-to-point;
}
interface ge-0/0/5.0 {
point-to-point;
}
interface lo0.0 {
passive;
}
}
}
security {
forwarding-options {
family {
iso {
mode packet-based;
}
}
}
policies {
from-zone SRX11 to-zone SRX13 {
policy ALLOW-ESP {
match {
source-address any;
destination-address any;
application ESP;
}
then {
permit;
}
}
policy ALLOW-IKE-500 {
match {
source-address any;
destination-address any;
application junos-ike;
}
then {
permit;
count;
}
}
policy ALLOW-PING {
match {
source-address any;
destination-address any;
application junos-icmp-ping;
}
then {
permit;
}
}
policy DENY-ALL {
match {
source-address any;
destination-address any;
application any;
}
then {
deny;
log {
session-init;
session-close;
}
count;
}
}
}
policy-rematch;
}
zones {
security-zone SRX11 {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
}
interfaces {
ge-0/0/4.0;
}
}
security-zone SRX13 {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
}
interfaces {
ge-0/0/5.0;
}
}
}
}
applications {
application ESP protocol esp;
}
SRX-13 configuration with IPSEC
interfaces {
ge-0/0/3 {
description "Connection to Server";
unit 0 {
family inet {
address 10.80.80.1/24;
}
}
}
ge-0/0/5 {
description "Connection to SRX-12";
unit 0 {
family inet {
address 172.18.2.13/24;
}
family iso;
}
}
lo0 {
unit 0 {
family inet {
address 192.168.13.13/32;
}
family iso {
address 49.0000.0000.0000.0013.00;
}
}
}
st0 {
unit 0 {
family inet {
address 192.168.1.13/24;
}
}
}
}
routing-options {
static {
route 192.168.200.0/24 next-hop 192.168.1.11;
}
}
protocols {
isis {
level 2 disable;
interface ge-0/0/5.0 {
point-to-point;
}
interface lo0.0 {
passive;
}
}
}
security {
ike {
proposal REKEY-ALOT {
authentication-method pre-shared-keys;
dh-group group1;
encryption-algorithm aes-128-cbc;
lifetime-seconds 180;
}
policy IKE-POL {
proposals REKEY-ALOT;
pre-shared-key ascii-text "$9$byY4ZHqfn/tUj/tuOcSwYgoUjk.PQ36"; ## SECRET-DATA
}
gateway SRX-11 {
ike-policy IKE-POL;
address 192.168.11.11;
external-interface lo0.0;
}
}
ipsec {
proposal SHORT_SA {
protocol esp;
authentication-algorithm hmac-md5-96;
encryption-algorithm aes-128-cbc;
lifetime-seconds 200;
}
policy IPSEC-POL {
proposals SHORT_SA;
}
vpn SRX-11 {
bind-interface st0.0;
ike {
gateway SRX-11;
ipsec-policy IPSEC-POL;
}
establish-tunnels on-traffic;
}
}
forwarding-options {
family {
iso {
mode packet-based;
}
}
}
policies {
from-zone TRUST to-zone TRUST {
policy ACCEPT-TRUST {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone UNTRUST to-zone UNTRUST {
policy ACCEPT-UNTRUST {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
zones {
security-zone UNTRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
ike;
}
}
interfaces {
ge-0/0/5.0;
lo0.0;
}
}
security-zone TRUST {
host-inbound-traffic {
system-services {
ping;
traceroute;
}
}
interfaces {
ge-0/0/3.0;
st0.0;
}
}
}
}